The last couple of weeks, I've been playing with Kali Linux to explore exploits on networks (wireless and switched networks). One of the exploits I'd liked to explore was that of an 'Evil Access Point' which can be done with Kali Linux and a suitable wireless LAN adapter.
My Evil Access Point creates an wireless network SSID to lure unsuspecting users/computers in to connecting to it. This network pretends to use 802.1x for security (which is mainly used in corporate network environments), and those networks require typically a user-name and password (or certificate) to connect.
When the user/computer tries to connect, it (the evil AP) collects the user-name and a hash of the password. The password can be recovered by using dictionary files, rainbow tables, or by using brute-force. After the password has been found it can be used with the captured user-name to connect to the corporate network.
The following video shows what the user experiences and what the hacker gets to see;
I used the hostapd-wpe version (which is a patched version of the regular hostapd package) to create the hostbased Access Point in the Kali Linux operating system. It creates a wireless SSID with 802.1x authentication based on PEAP/MSCHAPv2.
The warning that pops up in the video on the iPhone is a regular and legitimate warning. Every time you connect to a new wireless SSID with 802.1x enabled, it will ask the user to trust the actual RADIUS certificate. How many users actually verify the certificate? And how many of those actually verify the hashes, fingerprints etc?
A problem with the verification of this certificate (on the iPhone) is that you cannot verify the entire certificate chain (SSL Certificate -> Intermediate CA -> Root CA). You only see the SSL certificate, but you have no reference. This is bad.
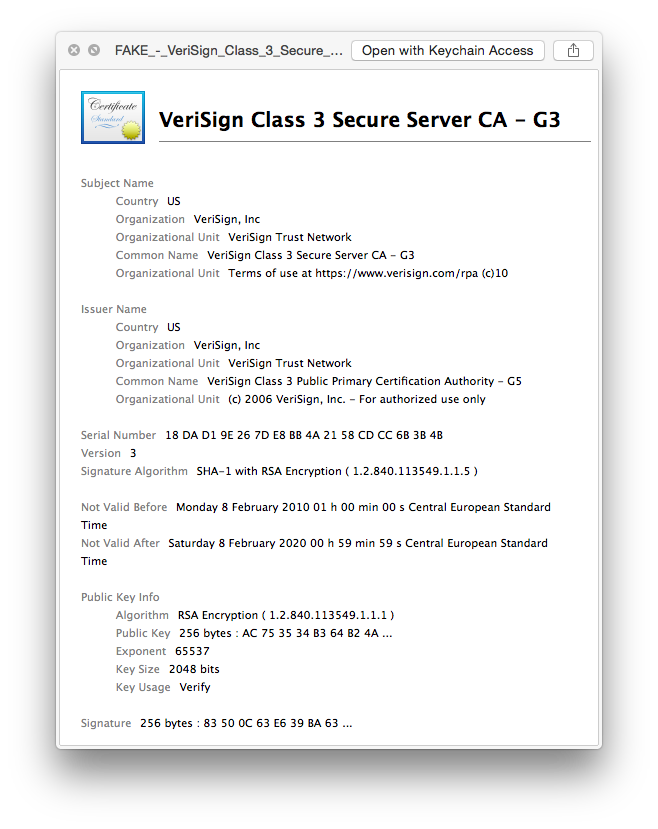
My test certificate is a fairly obvious false certificate, but it's not that hard to create an SSL certificate that looks a lot like e.g. a VeriSign certificate. The following screenshots show a fake VeriSign Root CA certificate, the intermediate Secure Server CA, and a new RADIUS certificate issued to radius.foobar.local that I created with XCA.
With the fake CA, I can issue fake SSL certificates that looks like that they have been issues by VeriSign. Sure, browsers and Operating Systems will issue warnings to the user (unless they trust it explicitly), but how many users actual pay attention to those warnings. And lets face it: it looks fairly real to the 'average Joe'...
There are some things that can be done to avoid this;
- Educate your users/employees on the dangers of connecting to wireless networks.
- Make sure the users are not allowed to accept warnings/errors while connecting to the wireless networks.
- Use provisioning (Mobile Device Management) tools to configure the mobile devices, so that users cannot connect to those unwanted/fake SSID's.
- Use EAP-TLS (802.1x authentication based on digital certificates) instead of PEAP/MSCHAPv2, because those are much harder to crack.
- and educate your users/employees on the dangers of connecting to wireless networks.
Tools used in this demonstration:
- Kali Linux (running in a VM on Windows 7)
- Patched version of hostapd (hostapd-wpe).
- Alfa Network AWUS036NEH 802.11bgn Long-Range USB adapter ( Ralink-R3070) (AWUS036NEH)
- Apple iPhone 5s with iOS8.3