This blog post hold the key ingredients for successfully authenticating on layer 2 (802.1x or dot1x) and layer 3 with:
- Junos Pulse supplicant
- Juniper Pulse Access Control Service a.k.a. Unified Access Control (UAC)
- Juniper EX2200 switch
- Microsoft Windows 7 Enterprise Edition
General Information
The setup consists of four networks (VLAN's) and Internet access. Inter-VLAN communication is handled by a Juniper SRX210. The four VLAN's are:
- Untrust (VLAN 20)
The Internet - Trust (VLAN 10 - 192.168.1.0/24)
This VLAN hosts the UAC, Active Directory, DNS and DHCP services - Production (VLAN 100 - 192.168.100.0/24)
Network where the normal workstations are placed - Quarantine (VLAN 200 - 192.168.200.0/24)
This is where the naughty people/PC's are dropped
When a PC is placed in Quarantine, it looses all access to the Internet, but can still resolve domain names, access minimal internal services like the DHCP server and the UAC.
The components on the network are:
- Domain Controller + DNS Server - 192.168.1.10
- DHCP Server - 192.168.1.1
- UAC - 192.168.1.11
- Gateway(s) - .254
Network overview
UAC Configuration
I will go through the menus of the UAC from top to bottom. Some configuration steps might be out-of-order, but makes it easier for me to describe them.
Certificate Configuration
UAC Certificate Information
I Installed an SSL certificate that was signed by my internal Root CA. The same root CA is trusted within the Active Directory Domain, and should therefore be trusted by all the clients in the domain.
Sign-in and Auth Servers
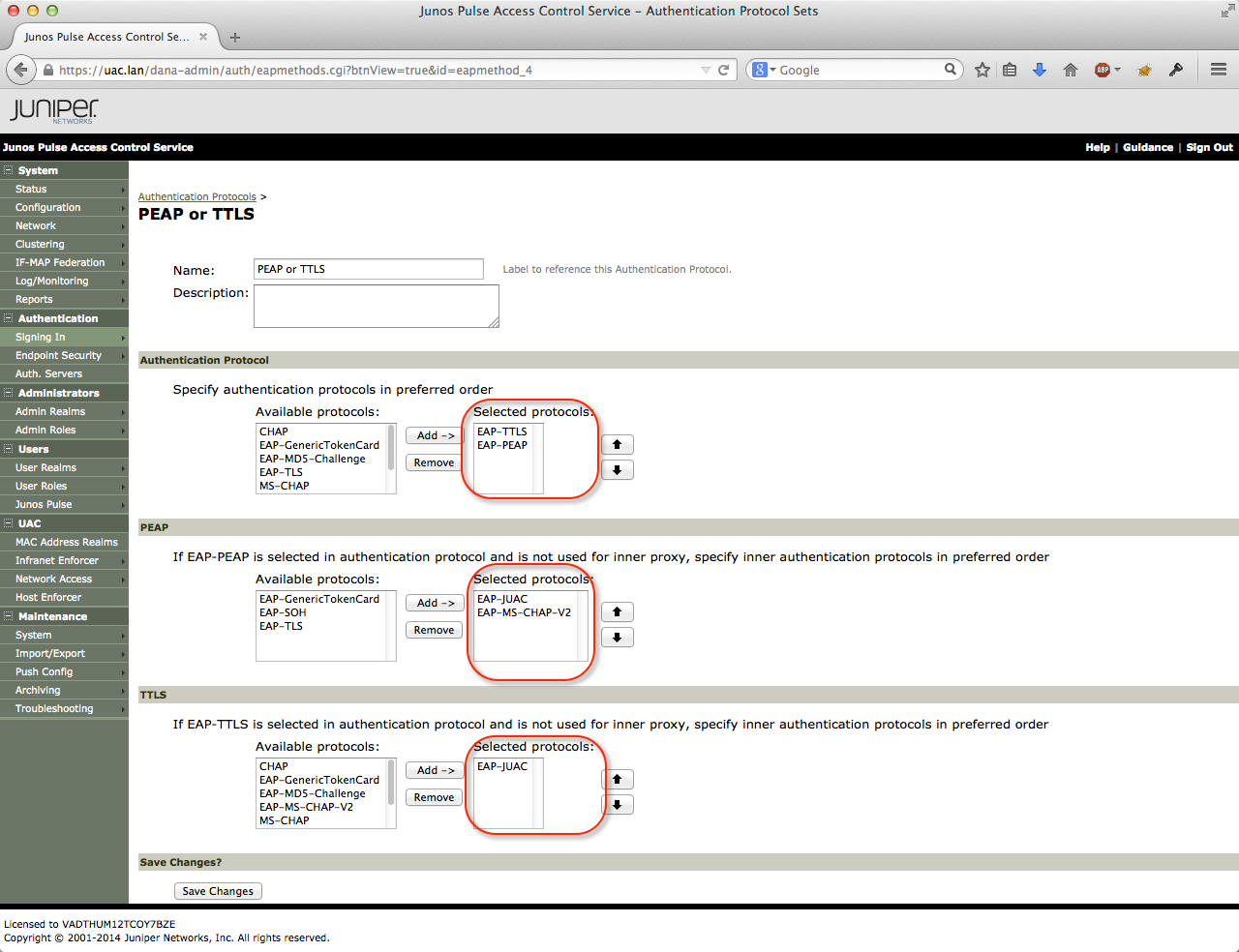
The Signing-In menu is modified to allow PEAP and EAP-TTLS for the dot1x clients. Other protocols are not allowed. EAP-TTLS is the only protocol that works with the host checker functionality. The PEAP protocol is only there because I need it in a future scenario, and I was to lazy to remove it from the config.
The realm configured for these protocols is the Testdomain Realm which uses a connection to the AD for domain user and domain machine authentication.
Endpoint Security
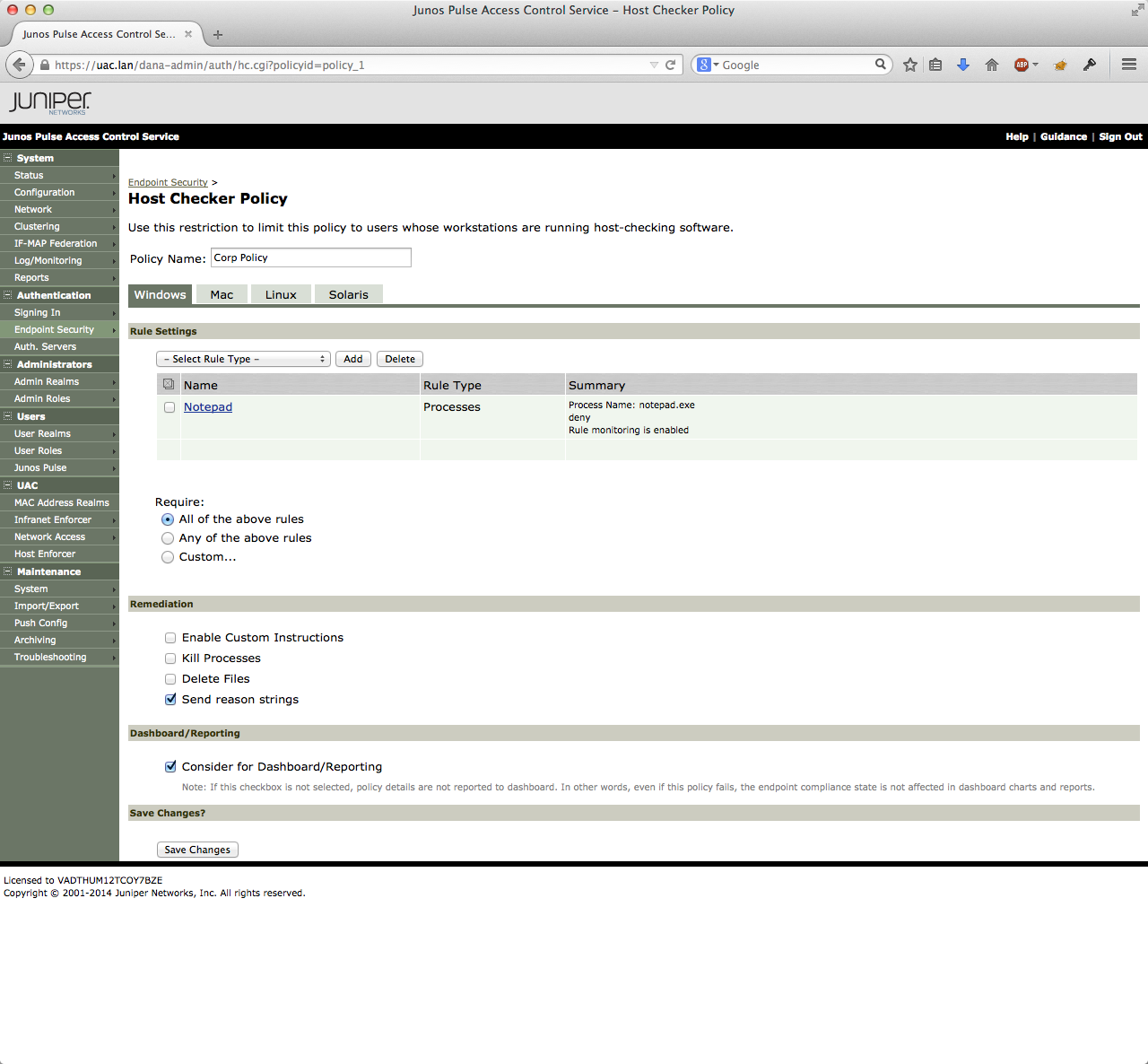
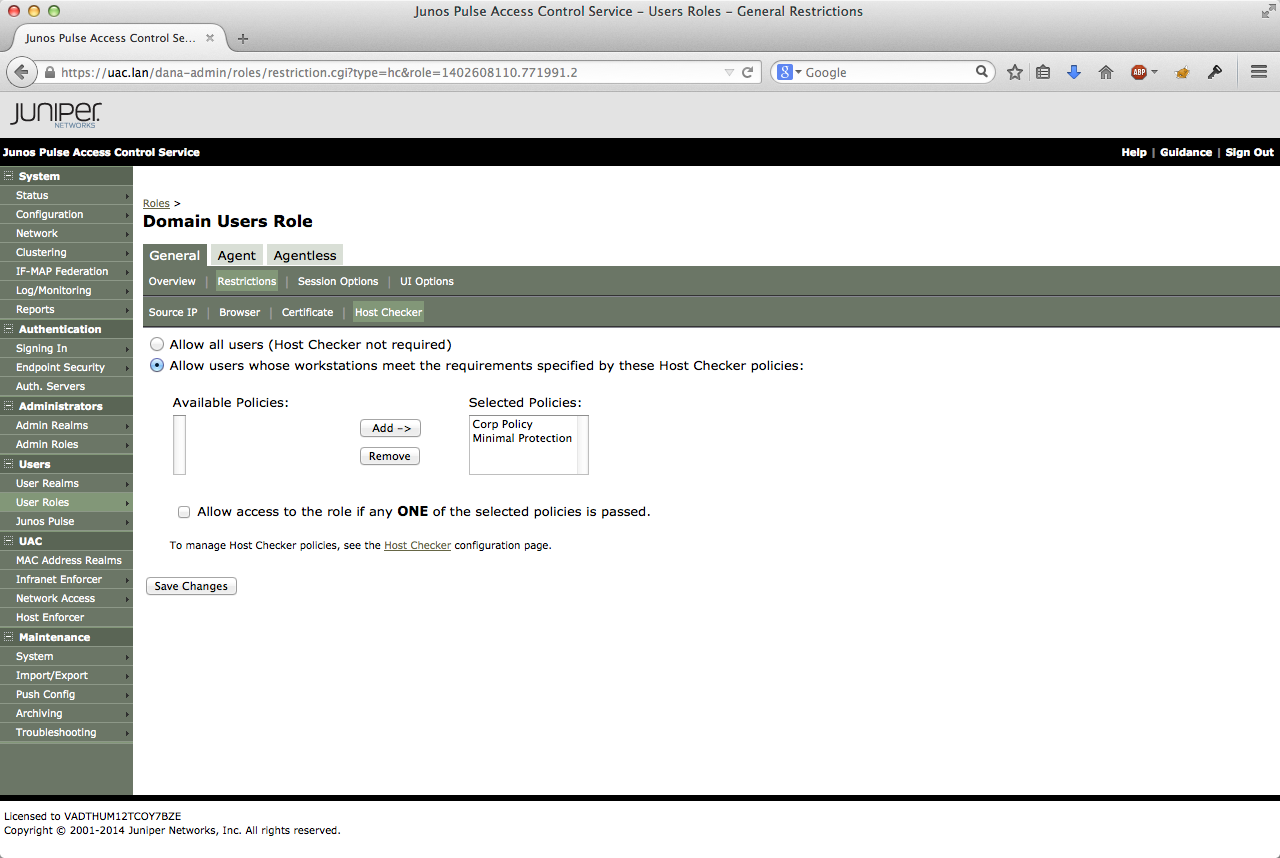
The host checker will be used to detect violations on the end-users PC. To trigger this manually, I created a rule that makes the UAC place the PC in quarantine when the user starts notepad.exe. The policy is called Corp Policy. The other policy checks for the existence of a known anti-virus program and a personal firewall on the Windows PC. Since simulating these requirements is relatively hard, so I created the notepad rule.
In the part where the results are shown (at the end of this blog post) is also a virus scanner violation shown. In that (accidental) case was the Full AV Scan on the PC not recent enough. So the scan needed to run before the PC got access to the production VLAN.
User Realms
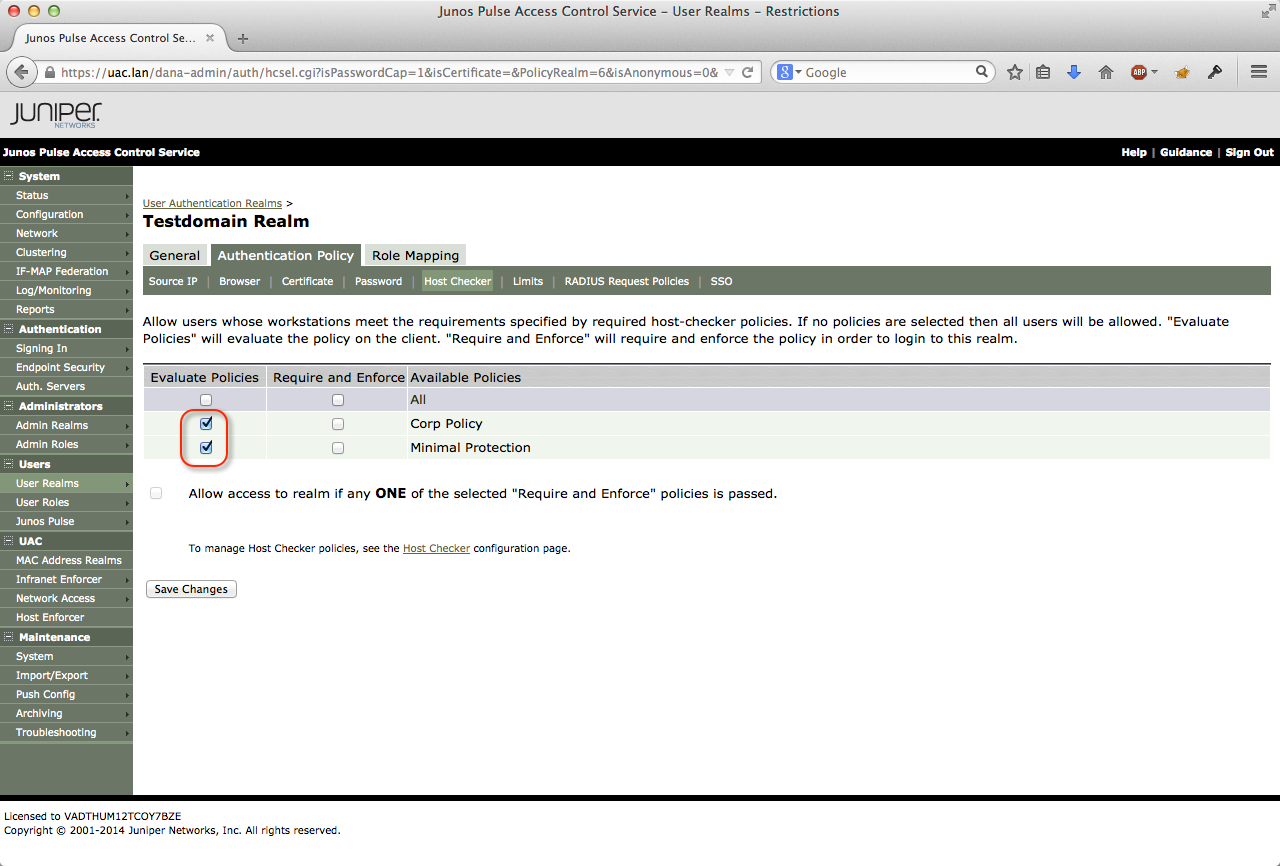
The user realm is called Testdomain Realm and uses the AD for authentication and authorization. The realm has the hostchecker policy set on evaluate in the restrictions submenu. This is necessary if you want to use these host check policies during the role mapping process.
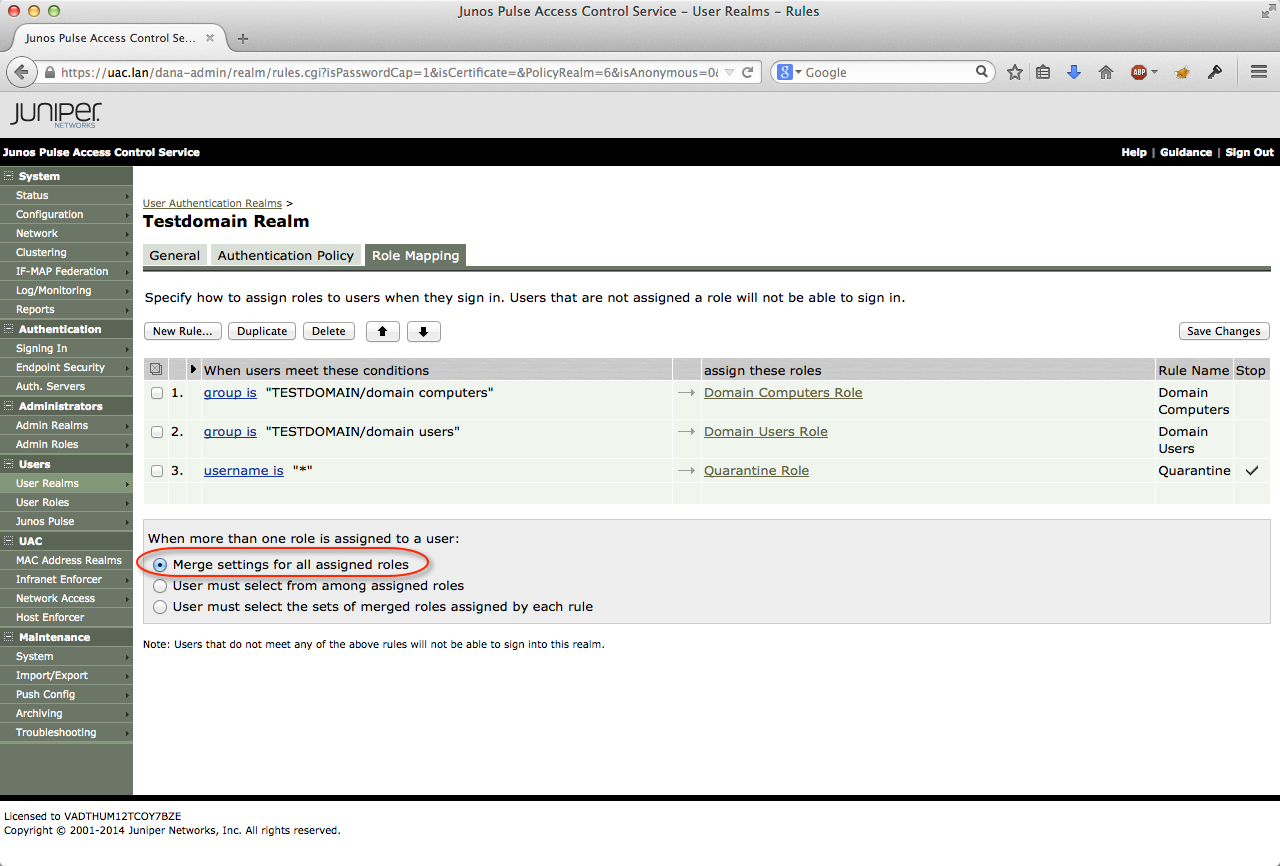
The role mapping process simple;
- Members of the Domain Computers security group in the Active Directory are mapped to the Domain Computer Role.
- Members of the Domain Users security group in the Active Directory are mapped to the Domain User Role.
- Everyone is mapped to the quarantine role (since the roles are merged).
Normally the other role will take precedence, but when a violation occurs the Quarantine role is the only one left and those settings will be enforced.
User Roles
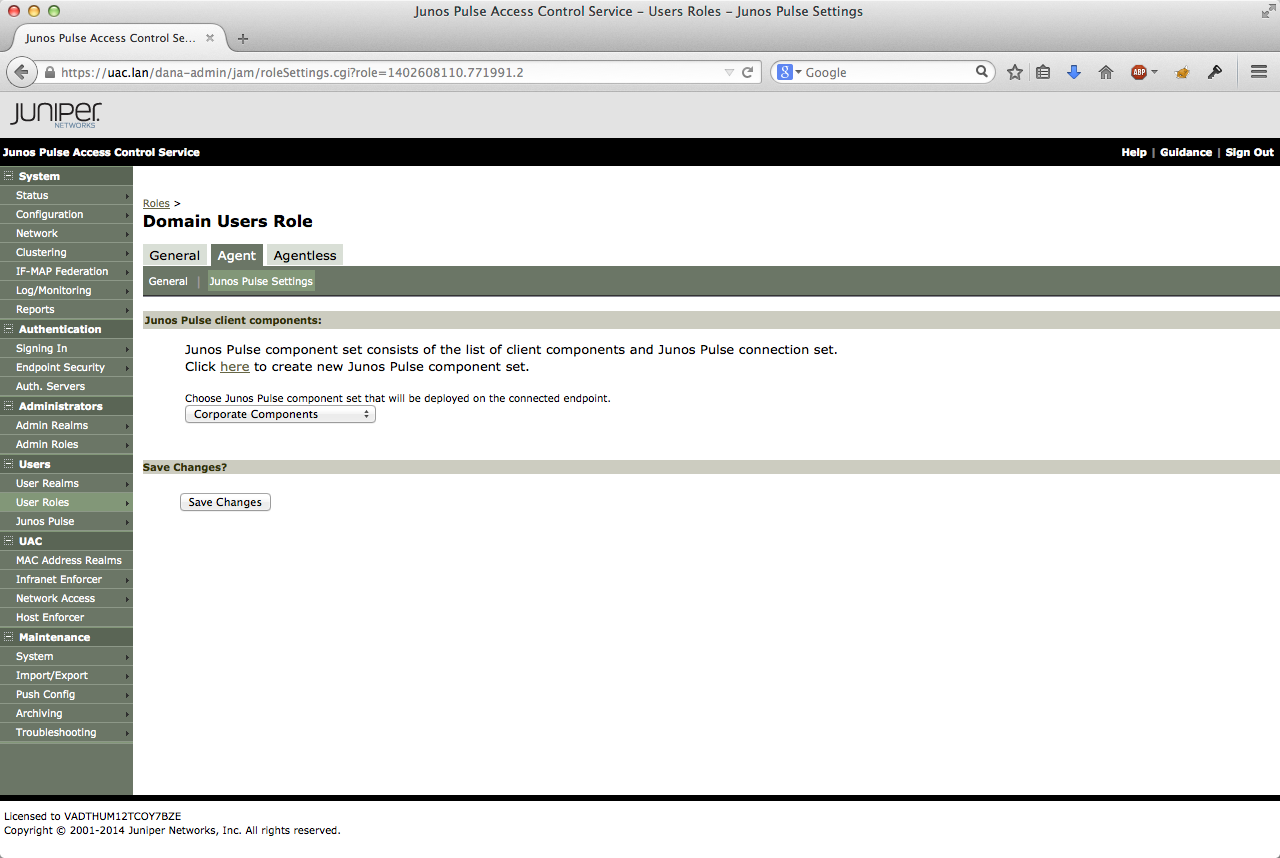
The user role definition includes the Host-checker requirements. It also defines if change of IP address is allowed, and what Junos Pulse settings (Connection Component Set) is used for that role.
I created separate roles for the Domain Computer and Domain User. The reason is that I want some host check functionalities be available only in the Computer 'space' (when no user is logged on). Examples are the use or existence of the firewall and/or AV software on the PC. These services start (when used correctly) as a service without the need for a logged in user. So you should make it a requirement that the firewall is active on a PC even when a user is not logged in to the machine. PC's can get compromised even when no user is logged in.
There are scenario's where it's not possible to check all requirements within one role/hostchecker policy. E.g. the use of torrent clients is something that usually occurs in the user space on the PC. When you check this at the machine-level (only), you're gonna miss it when the user launches the software from the desktop.
In this case I want to avoid that people launch notepad.exe and still be able to access the Internet.
Pulse Client Configuration
The Pulse client is configured to do machine and user authentication. The user part takes over when the user logs in to the desktop. For the Layer 2 connection to the UAC I trusted the CA that issued the SSL certificate of the UAC. The Layer 3 connection relies on certificate issuer trust settings in the OS or browser (depending on the platform).
RADIUS Clients / Return Attributes
The last step (in this case) is to add the switch a RADIUS client and configure the RADIUS return attributes when an authentication or change in authorization happens.
In this case I attached return attributes Production VLAN 100 for the Domain Users and Domain Computers, and VLAN 200 for the Quaratine VLAN.
Windows PC Configuration
The Windows 7 OS was default with only the usual Windows updates installed. The network adapter had 802.1x enabled on the wired interface, and was set for PEAP authentication (default settings). The PC was joined to the testdomain.local AD with an administrator account. The PC was connected to a switch port which was configured with a static production VLAN membership (no dot1x at that moment).
Junos Pulse connected to the network
After logging in with a AD domain user account (andy), I used Internet Explorer to access the sign-in URL on the UAC (https://uac.testdomain.local). Logged in with the username (Andy) and I got pushed the Junos Pulse client (you need admin access if you want to install Pulse on the PC). After the installation I shut down the PC and moved the network cable to the dot1x port on the switch, and started the OS.
After the reboot the Junos Pulse client connected to the network, and the PC was placed in the correct VLAN (production VLAN id = 100). Check the logging at the end of this blog for confirmation.
Switch Configuration
Below is the (relevant) part of the Juniper EX220 switch configuration (including the Junos software version).
version 12.3R6.6;
interfaces {
ge-0/0/0 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
ge-0/1/0 {
description "Uplink to srx210 ge-0/0/0";
mtu 9216;
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members [ vlan-trust vlan-untrust vlan-production vlan-quarantine ];
}
}
}
}
protocols {
dot1x {
authenticator {
authentication-profile-name UAC;
no-mac-table-binding;
interface {
ge-0/0/0.0 {
supplicant multiple;
retries 6;
transmit-period 20;
reauthentication 180;
supplicant-timeout 20;
server-timeout 15;
maximum-requests 6;
server-fail use-cache;
}
}
}
}
}
access {
radius-server {
192.168.1.11 {
port 1812;
secret "<SHARED_SECRET>"; ## SECRET-DATA
source-address 192.168.1.51;
}
}
profile UAC {
authentication-order radius;
radius {
authentication-server 192.168.1.11;
}
}
}
vlans {
default {
vlan-id 1;
}
vlan-trust {
vlan-id 10;
}
vlan-untrust {
vlan-id 20;
}
vlan-production {
vlan-id 100;
no-local-switching;
}
vlan-quarantine {
vlan-id 200;
no-local-switching;
}
}Simulating A Violation
The host checker was configured to require a valid virus scanner and an active personal firewall. This rule was mandatory for the machine AND user account. When this is not satisfactory, the machine will be placed in quarantine. An extra rule was added that checked on a running program called notepad.exe. When this is detected, the PC will be placed in quarantine. It's that last rule that I use to check if thing work as advertised.
The thing is that I encountered issues on several occasions with the known AV software. One weird update of the virus scanner might screw things up in a big way. Especially when Pulse doesn't recognise the AV software (or AV definitions) after an update......
That's something for Juniper Support (JTAC) and/or the AV vendor to figure out.
The Results
The following YouTube video shows what happens on the PC;
- Continuous ping to 8.8.8.8 (Google DNS) and the internal UAC (192.168.1.11) work. The IP address on the network adapter is 192.168.100.x (Production VLAN)
- The Junos Pulse client states that the PC is compliant.
- Notepad.exe is launched
- Junos Pulse detects notepad.exe and the PC is placed in the quarantine VLAN by the UAC.
- IP Address becomes 192.168.200.x (Quarantine VLAN).
- Continuous ping to Google DNS stops (8.8.8.8), but the internal UAC is still reachable.
- Notepad.exe is closed
- Junos Pulse detects the change and declares the PC compliant again.
- The PC is switched back to the production VLAN, and the continous ping to Google DNS (8.8.8.8) is resumed.
Note: During the VLAN switch there are some packets that get lost. This is normal behaviour. Expect at least 1 or 2 pings to go missing during the transition.
The booting of the PC WIN7-VM (with the machine account authentication), the log-in of the user (andy) and the creation of the violation is recorded in the logging of the UAC and shown below.
2014-08-05 14:00:55 - ic - [127.0.0.1] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[] - Primary authentication successful for TESTDOMAIN\WIN7-VM$/TESTDOMAIN AD SERVER from 00-11-6b-66-3d-22 2014-08-05 14:00:58 - ic - [127.0.0.1] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[] - Host Checker policy 'Corp Policy' passed on host for user 'TESTDOMAIN\WIN7-VM$'. 2014-08-05 14:00:58 - ic - [127.0.0.1] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[] - Host Checker policy 'Minimal Protection' passed on host for user 'TESTDOMAIN\WIN7-VM$'. 2014-08-05 14:00:58 - ic - [127.0.0.1] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[Domain Computers Role, Quarantine Role] - Agent login succeeded for TESTDOMAIN\WIN7-VM$/Testdomain Realm from 00-11-6b-66-3d-22. 2014-08-05 14:00:58 - ic - [127.0.0.1] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[Domain Computers Role, Quarantine Role] - User assigned to vlan (VLAN='100') 2014-08-05 14:00:58 - ic - [127.0.0.1] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[Domain Computers Role, Quarantine Role] - RADIUS authentication accepted for TESTDOMAIN\WIN7-VM$ (realm 'Testdomain Realm') from location-group 'Default' and attributes are: NAS-IP-Address = 192.168.1.51,NAS-Port = 70,NAS-Port-Type = 15 2014-08-05 14:00:58 - ic - [192.168.100.103] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[] - Primary authentication successful for TESTDOMAIN\WIN7-VM$/TESTDOMAIN AD SERVER from 192.168.100.103 2014-08-05 14:01:00 - ic - [192.168.100.103] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[] - Host Checker policy 'Corp Policy' passed on host 192.168.100.103 for user 'TESTDOMAIN\WIN7-VM$'. 2014-08-05 14:01:00 - ic - [192.168.100.103] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[] - Host Checker policy 'Minimal Protection' passed on host 192.168.100.103 for user 'TESTDOMAIN\WIN7-VM$'. 2014-08-05 14:01:00 - ic - [192.168.100.103] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[Domain Computers Role, Quarantine Role] - Agent login succeeded for TESTDOMAIN\WIN7-VM$/Testdomain Realm from 192.168.100.103. 2014-08-05 14:01:17 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[] - Primary authentication successful for TESTDOMAIN\andy/TESTDOMAIN AD SERVER from 00-11-6b-66-3d-22 2014-08-05 14:01:19 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[] - Host Checker policy 'Corp Policy' passed on host for user 'TESTDOMAIN\andy'. 2014-08-05 14:01:19 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[] - Host Checker policy 'Minimal Protection' passed on host for user 'TESTDOMAIN\andy'. 2014-08-05 14:01:19 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Agent login succeeded for TESTDOMAIN\andy/Testdomain Realm from 00-11-6b-66-3d-22. 2014-08-05 14:01:19 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - User assigned to vlan (VLAN='100') 2014-08-05 14:01:19 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - RADIUS authentication accepted for TESTDOMAIN\andy (realm 'Testdomain Realm') from location-group 'Default' and attributes are: NAS-IP-Address = 192.168.1.51,NAS-Port = 70,NAS-Port-Type = 15 2014-08-05 14:01:19 - ic - [192.168.100.103] TESTDOMAIN\WIN7-VM$(Testdomain Realm)[Domain Computers Role, Quarantine Role] - Logout from 192.168.100.103 (session:ff384a65) 2014-08-05 14:01:20 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[] - Primary authentication successful for TESTDOMAIN\andy/TESTDOMAIN AD SERVER from 192.168.100.103 2014-08-05 14:01:21 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[] - Host Checker policy 'Corp Policy' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:01:21 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[] - Host Checker policy 'Minimal Protection' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:01:21 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Agent login succeeded for TESTDOMAIN\andy/Testdomain Realm from 192.168.100.103. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Roles for user TESTDOMAIN\andy on host 192.168.100.103 changed from <Domain Users Role,Quarantine Role> to <Quarantine Role> during policy reevaluation. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Corp Policy' failed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. Reason: 'Rule-Notepad:found notepad.exe'. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Roles for user TESTDOMAIN\andy on host 192.168.100.103 changed from <Domain Users Role,Quarantine Role> to <Quarantine Role> during policy reevaluation. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Corp Policy' failed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. Reason: 'Rule-Notepad:found notepad.exe'. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Corp Policy' failed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. Reason: 'Server has not received any information for this policy.'. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Minimal Protection' failed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. Reason: 'Server has not received any information for this policy.'. 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Forcing off user (TESTDOMAIN\andy) because of change in VLAN/RADIUS Attributes policy 2014-08-05 14:05:01 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - User assigned to vlan (VLAN='200') 2014-08-05 14:05:01 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - RADIUS authentication was resumed for TESTDOMAIN\andy (realm 'Testdomain Realm') from location-group 'Default' and attributes are: NAS-IP-Address = 192.168.1.51,NAS-Port = 70,NAS-Port-Type = 15 2014-08-05 14:05:02 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Remote address for user TESTDOMAIN\andy/Testdomain Realm changed from 192.168.100.103 to 192.168.200.102. 2014-08-05 14:05:02 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Session resumed from user agent 'Junos-Pulse/8.0.5.47721 (Windows 7)' 2014-08-05 14:05:02 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Remote address for user TESTDOMAIN\andy/Testdomain Realm changed from 192.168.100.103 to 192.168.200.102. 2014-08-05 14:05:04 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:04 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Corp Policy' failed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. Reason: 'Rule-Notepad:found notepad.exe'. 2014-08-05 14:05:06 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:06 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Corp Policy' failed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. Reason: 'Rule-Notepad:found notepad.exe'. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Roles for user TESTDOMAIN\andy on host 192.168.200.102 changed from <Quarantine Role> to <Domain Users Role,Quarantine Role> during policy reevaluation. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Corp Policy' passed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Roles for user TESTDOMAIN\andy on host 192.168.200.102 changed from <Quarantine Role> to <Domain Users Role,Quarantine Role> during policy reevaluation. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Corp Policy' passed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.200.102 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:31 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Forcing off user (TESTDOMAIN\andy) because of change in VLAN/RADIUS Attributes policy 2014-08-05 14:05:33 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - User assigned to vlan (VLAN='100') 2014-08-05 14:05:33 - ic - [127.0.0.1] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - RADIUS authentication was resumed for TESTDOMAIN\andy (realm 'Testdomain Realm') from location-group 'Default' and attributes are: NAS-IP-Address = 192.168.1.51,NAS-Port = 70,NAS-Port-Type = 15 2014-08-05 14:05:34 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Remote address for user TESTDOMAIN\andy/Testdomain Realm changed from 192.168.200.102 to 192.168.100.103. 2014-08-05 14:05:34 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Session resumed from user agent 'Junos-Pulse/8.0.5.47721 (Windows 7)' 2014-08-05 14:05:34 - ic - [192.168.200.102] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Remote address for user TESTDOMAIN\andy/Testdomain Realm changed from 192.168.200.102 to 192.168.100.103. 2014-08-05 14:05:36 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Corp Policy' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:36 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:38 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Corp Policy' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'. 2014-08-05 14:05:38 - ic - [192.168.100.103] TESTDOMAIN\andy(Testdomain Realm)[Domain Users Role, Quarantine Role] - Host Checker policy 'Minimal Protection' passed on host 192.168.100.103 for user 'TESTDOMAIN\andy'.
I also got an accidental screenshot of what happens when the AV host checker policy fails. The PC will be assigned the quarantine VLAN for as long as the scan takes. When it finishes, the Pulse client will communicate the results with the UAC, and the PC is placed in the correct (production) VLAN.
Junos Pulse Remediation in action.
What's next?
The next related blog post will go into the layer 3 enforcement on a Juniper SRX by using dynamic firewall rules. The PC still need dot1x to gain access to the network, but when a violation is detected, the firewall rules for that PC are dynamically changed by the UAC. This saves you at least one VLAN in the network, but it does requires a Juniper SRX Firewall in the core of your network.
A nice feature of this is that you can mix different types of devices in one VLAN. Just restrict the traffic based on the identity of the user/machine.
After that, I'll add Intrusion Detection and Prevention to detect malicious traffic, and limit the PC's network accessibility accordingly.
The content of this blog post lays the foundation for that.