Juniper started to migrate their firewalls from Netscreen to the Junos environment 'a couple of' months back. The advantage is that there's a universal OS for routers, switches and firewalls. Just like Cisco IOS. The disadvantage is that the Junos OS is being adapted for the firewalls. So the foundations are there, but there are still lots of features missing and bugs are also still abundant.
The bugs are thankfully mostly related to the WebGUI. On the commandlinethe bugs are in the same league as the Cisco, Checkpoint and every other vendor bugs. No piece of software is perfect.
Anyway, starting with the SRX Firewalls, it's handy to see what's happening by viewing the (firewall security) logfiles.
To enable the logging (which is disabled by default......) you can do the following:
DISCLAIMER: The following information is based on JUNOS 10.4R1.9 for the Juniper SRX100H
WebGUI
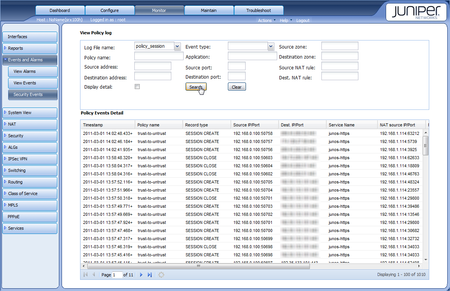
- Log on to webGUI and open the Monitor 'tab'
- Expand the Event and Alarms menu
- Select the Security Events page.
- Press the 'Create Log Configuration' button
This will create the logging configuration (Log File Name: policy_session). The filename is fixed, and should not be changed.
The policy_session logfile has been createdAfter this you need to enable logging / counting on the specific firewall security rules.
Enable Logging / Counting on the Security Firewall PoliciesAfter this, you can view the logging in the WebGUI by going to: Monitor -> Events and Alarms -> Security Events and press the search button.
Viewing Security logging in the WebGui
CLI
The other way of enabling the logging is by enabling it on the commandline. Again, the 'policy_session' filename should not be changed. I've experienced weird behaviour (on the logging part) by changing it.
[edit]
root# set system syslog file policy_session user info
root# set system syslog file policy_session match RT_FLOW
root# set system syslog file policy_session archive size 1000k
root# set system syslog file policy_session archive world-readable
root# set system syslog file policy_session structured-data
This will result in the following (the bold parts are added by these lines):
[edit]
root# run show configuration system syslog
syslog {
archive size 100k files 3;
user * {
any emergency;
}
file messages {
any critical;
authorization info;
}
file interactive-commands {
interactive-commands error;
}
file policy_session {
user info;
match RT_FLOW;
archive size 1000k world-readable;
structured-data;
}
}